areia-lab / laravel-traffic-control
Traffic control toolkit for Laravel — advanced throttling, blocking, bot detection, analytics, and dashboard.
Package info
github.com/areia-lab/laravel-traffic-control
Language:Blade
pkg:composer/areia-lab/laravel-traffic-control
Requires
- php: >=8.0
- illuminate/support: ^9.0|^10.0|^11.0|^12.0
This package is auto-updated.
Last update: 2026-02-11 13:13:55 UTC
README
A full-featured traffic control & security toolkit for Laravel.
It provides rate limiting, IP black/whitelisting, bot detection, request quotas, alerts, logging, and a monitoring dashboard.
✨ Features
- 🔒 Advanced Rate Limiting (per-IP, per-user, per-route, per-role, per-plan)
- 🌍 IP Control: Whitelist, Blacklist, TOR/VPN blocking
- 🤖 Bot & Crawler Detection using User-Agent patterns
- 📊 Traffic Dashboard: Visualize blocked/allowed requests
- 📑 Logging of suspicious/blocked requests with purge command
- 🔔 Alerts (Slack, Email) on suspicious spikes
- 🚦 API Quotas (daily, monthly, per-user, per-plan)
- 🧩 Custom Rules: Extend with your own blocking logic (GeoIP, maintenance windows, etc.)
- ⚡ Request Queueing (optional future feature)
📦 Installation
Install via Composer:
composer require areia-lab/laravel-traffic-control
Publish configuration and migrations:
php artisan vendor:publish --provider="AreiaLab\TrafficControl\TrafficControlServiceProvider" --tag="traffic-config" php artisan vendor:publish --provider="AreiaLab\TrafficControl\TrafficControlServiceProvider" --tag="traffic-migrations" php artisan migrate
(Optional) Publish dashboard views:
php artisan vendor:publish --provider="AreiaLab\TrafficControl\TrafficControlServiceProvider" --tag="traffic-views"
📸 Screenshots
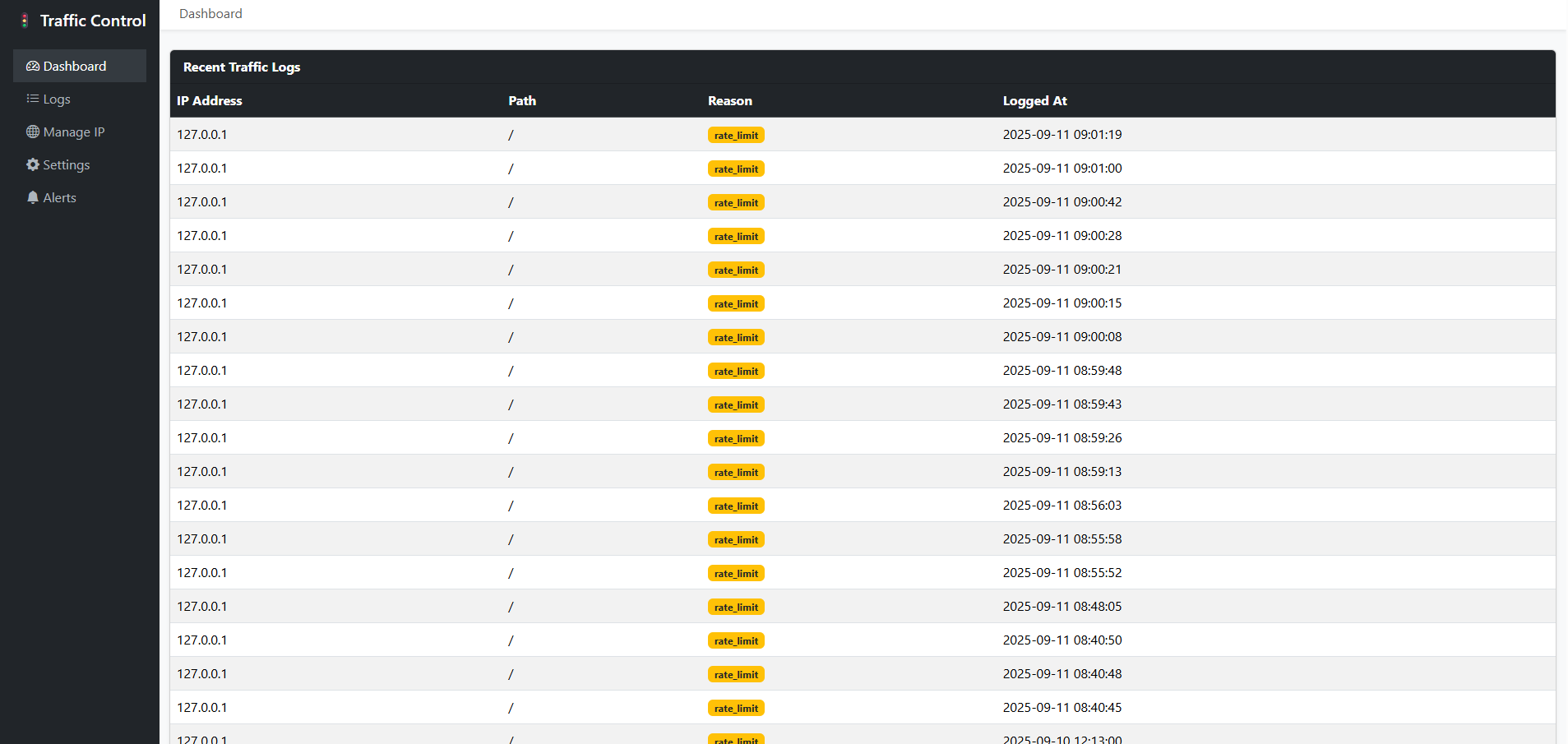
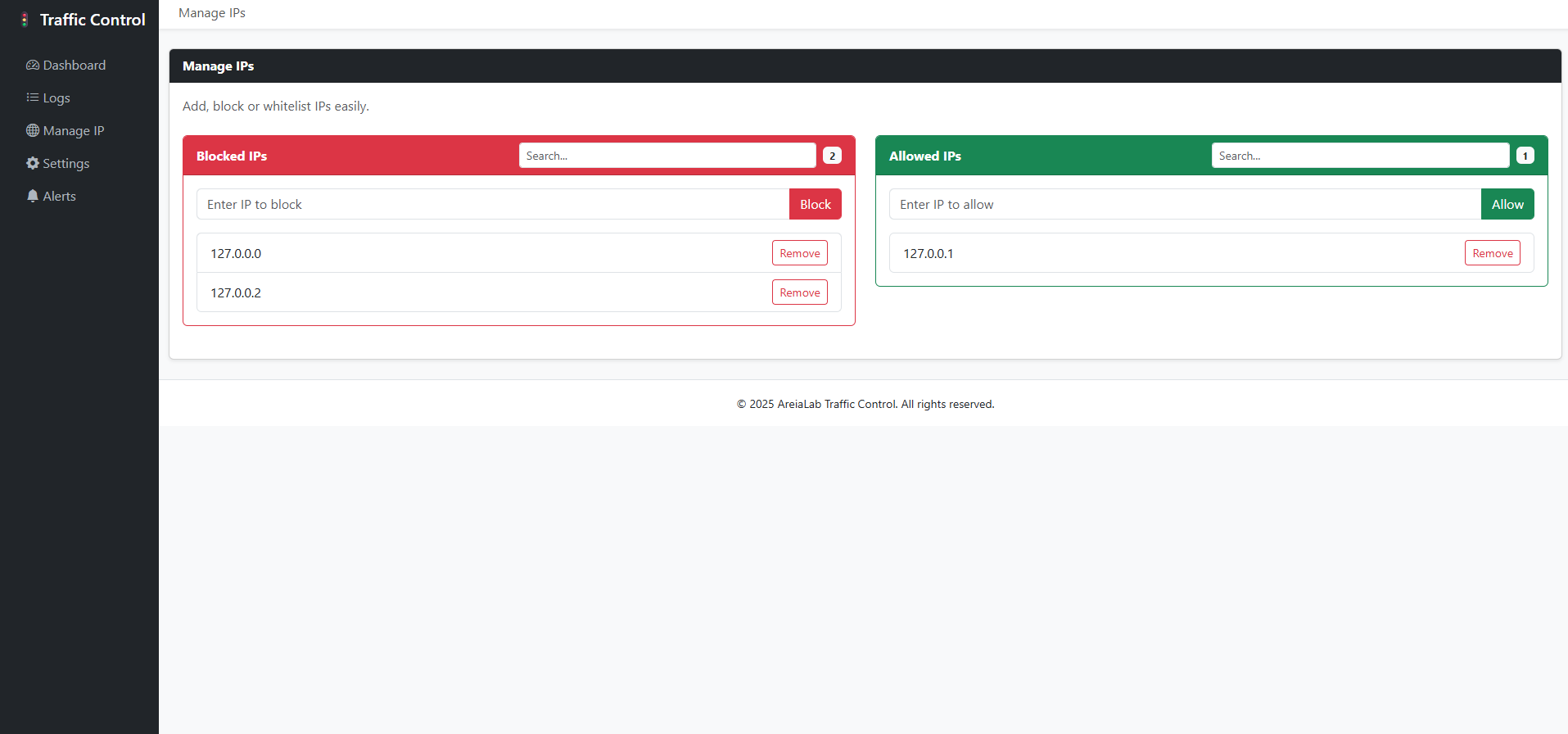
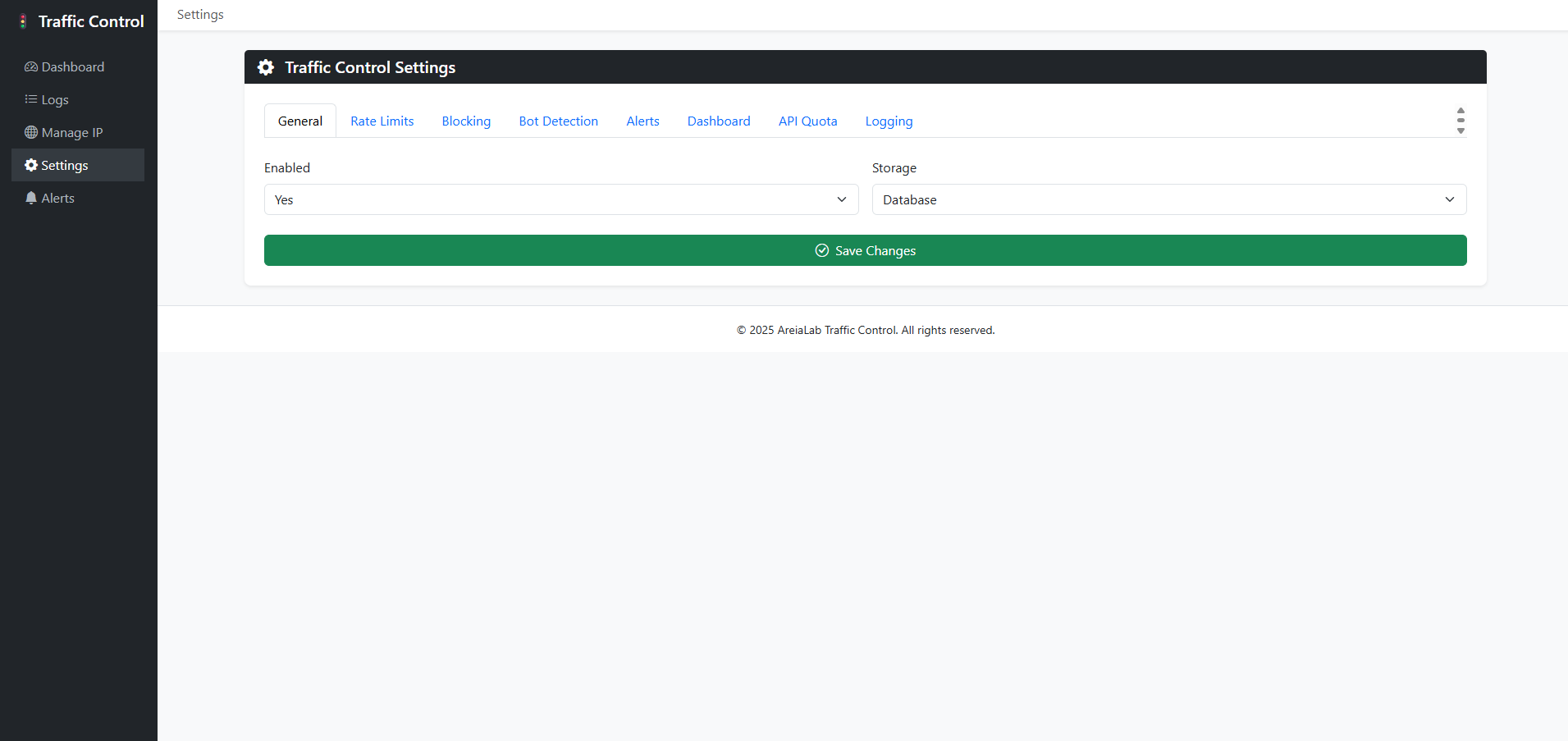
⚙️ Configuration
Edit config/traffic.php:
return [ 'enabled' => env('TRAFFIC_CONTROL_ENABLED', true), // Enable/disable globally 'storage' => env('TRAFFIC_CONTROL_STORAGE', 'redis'), // redis | database | file 'rate_limits' => [ 'default' => ['requests' => 60, 'per' => 60], 'api' => ['requests' => 120, 'per' => 60], ], 'ip' => [ 'block_tor' => true, 'blacklist' => [], 'whitelist' => [], ], 'bot_detection' => [ 'enabled' => true, 'user_agents' => ['bad-bot'], ], 'alerts' => [ 'slack' => env('TRAFFIC_CONTROL_SLACK_WEBHOOK'), 'email' => env('TRAFFIC_CONTROL_ALERT_EMAIL', 'admin@example.com'), 'threshold' => env('TRAFFIC_CONTROL_ALERT_THRESHOLD', 1000), ], 'dashboard' => [ 'enabled' => true, 'prefix' => 'traffic-control', 'middleware' => ['web'], ], 'api_quota' => [ 'default' => 10000, ], 'logging' => [ 'log_blocked' => true, 'log_sample_rate' => 1, ], ];
🚀 Usage
Middleware
Apply globally in app/Http/Kernel.php or per route:
Route::middleware(['traffic.control'])->group(function () { Route::get('/api/data', [ApiController::class, 'index']); });
Custom per-route limit:
Route::get('/heavy', [HeavyController::class, 'index']) ->middleware('traffic.control:200,60');
Role/Plan-Based Limits
if ($user = $request->user()) { $plan = $user->plan ?? 'free'; $limit = config("traffic-control.rate_limits.$plan", config('traffic-control.rate_limits.default')); }
API Quotas
use AreiaLab\TrafficControl\Facades\TrafficManager; if (!TrafficManager::checkQuota($user->id)) { return response()->json(['error' => 'API quota exceeded'], 429); }
Dashboard
Route::get('/admin/traffic', function () { $logs = \AreiaLab\TrafficControl\Models\TrafficLog::latest()->limit(50)->get(); return view('vendor.traffic-control.dashboard', compact('logs')); })->middleware(['web', 'auth'])->name('traffic-control.dashboard');
Alerts
Set .env variables:
TRAFFIC_CONTROL_SLACK_WEBHOOK=https://hooks.slack.com/services/XXXX
TRAFFIC_CONTROL_ALERT_EMAIL=admin@example.com
Purging Logs
php artisan traffic-control:purge # Purge logs older than 30 days
php artisan traffic-control:purge --days=90 --force
php artisan traffic-control:purge --all
php artisan traffic-control:purge --all --force
🧩 Extending
Create custom rules under src/Rules/:
namespace AreiaLab\TrafficControl\Rules; use Illuminate\Http\Request; class GeoBlockRule { public function handle(Request $request) { $country = $this->lookupCountry($request->ip()); if (in_array($country, ['CN', 'RU'])) { return response('Not available in your region', 403); } return true; } protected function lookupCountry($ip) { return 'US'; } }
🛠 Roadmap
- Redis sliding window / leaky bucket limiter
- GeoIP/TOR/VPN detection integration
- Charts for dashboard
- Plan-based quota & billing hooks
- AI anomaly detection
🤝 Contributing
PRs are welcome!
- Follow PSR-12 coding style
- Add unit/feature tests
- Update README.md when adding new features
📜 License
MIT © AreiaLab
